Recent Posts?

This page will discuss the various resources Wireshark has made available for the cybersecurity .
WiresharkWireshark is een van de toonaangevende tools op het gebied van cyberbeveiliging op het gebied van het vastleggen en analyseren van pakketten.

Wıreshark Wireshark installation
• Instant monitoring of network traffic
• To record this monitored traffic.
• It allows it to be reviewed later.
• Apart from these, it can also be used to solve an error. (This operation
The problem is tried to be detected by monitoring the traffic and using instant filtering solutions.)
The most important features of the Wireshark tool:
• User friendly
• Free to use
• Broad protocol support
• You can follow this link to see the supported protocols.
• https://wiki.wireshark.org/ProtocolReference
• Providing support for multiple operating systems:
• Windows
• Linux
• macOS
• Packet filtering support according to many criteria
• Capable of recording captured packets in various formats
• Ability to generate various statistics
• It has a lot of attention-grabbing features such as instant packet capture and viewing.
Uses of Wireshark tool:
• Resolving protocol errors
• Package analysis processes
• Detecting errors in the network
• To be able to view statistics about the network
• Live data or data in formats such as pcap you have view
• It is a preferred tool in many different subjects such as reverse engineering studies.
Minimum system requirements for Wireshark tool:
In order for you to run this tool on your computer in a healthy way, the following You must meet the system requirements:
• 400 Mhz processor
• 60 MB free space
• Promiscuous mode supported network card
• WinPcap driver
Here is the part that does the actual work for the Wireshark tool:
• It is the part that captures the instant network traffic and sends it to the wireshark tool.
• Wireshark tool also allows you to manage this network traffic (packet) thanks to its user-friendly interface. allows you to see the flow
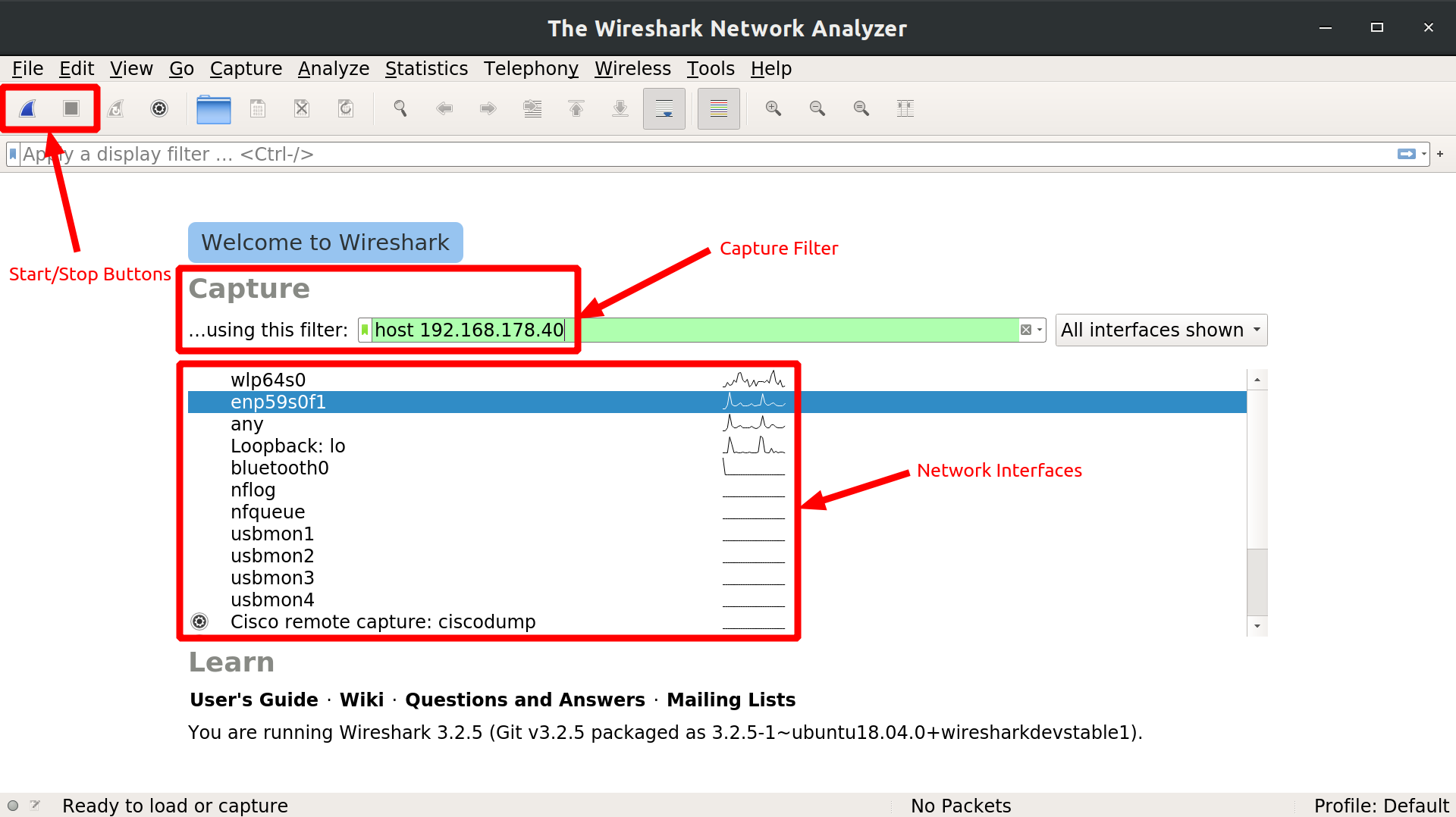
Packet capture with Wireshark tool
You have two options for this process. But what we should not forget is to run the Wireshark tool with root (the most authorized) person rights. This is because the wireshark tool wants to access our network cards.
1 ) To access the following menu by following the Capture -> Options path from the main menu
2) In this option, on the screen that welcomes you at the first opening of the program, click on the desired network card from the section indicated by the number 2 on the previous slide.
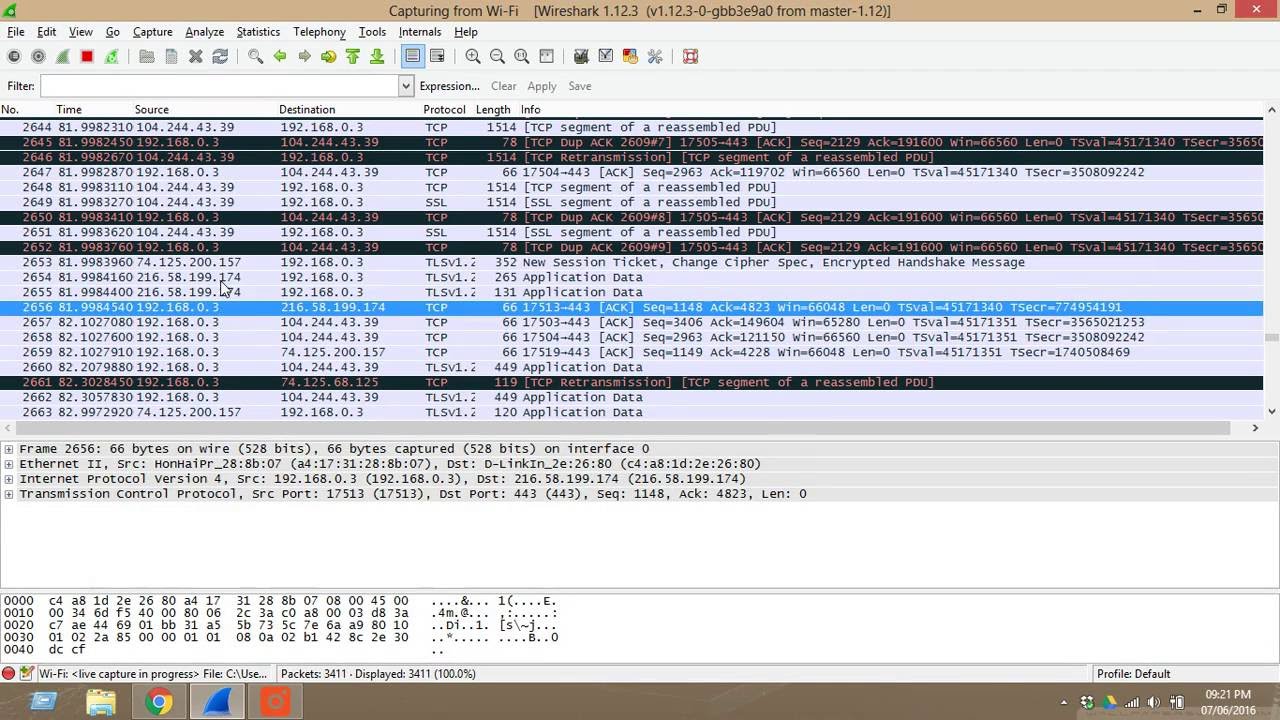
Let's get to know the interface in packet capture with Wireshark tool When the packet capture process starts, a layered interface will welcome us.
This is the section where the filtering options for the captured packets are found.
1 ) To access the following menu by following the Capture -> Options path from the main menu
2) This is the part where the captured packets are listed.
3) When we select one of the captured packets, the details about it is the part where it is displayed.
4) Shows the hex dump for the selected package.
5) It is the part where general information is included. In this section :
• Total packets captured
• Number of packages displayed
Filters:
A) DHCP
• port 67 or port 68
• bootp
• bootp.option.dhcp == 1 (DISCOVER Packets)
• bootp.option.dhcp == 2 (OFFER Packets)
• bootp.option.dhcp == 3 (REQUEST Packets)
• bootp.option.dhcp == 4 (ACK Packets)
• bootp.option.hostname
• port 67 or port 68
B) HTTP
• http
• http.request.method=="GET”
• http.request.method==”POST”
• http.response.code == “200”
• http.user_agent == “User_Agent_Value”
• http.referer
C) ARP
• arp
• arp.src.hw_mac == “Resource MAC address”
• arp.dst.hw_mac == “Target MAC address”
• arp.duplicate-address-frame
• arp.opcode == 1
• arp.opcode == 2
D) DNS
• dns.qry.name == "google.com”
• “dns.qry.type == 1 (A Record Type)dns.qry.type == 255 (ANY Record Type)
• dns.qry.type == 2 (NS name server)dns.qry.type == 15(MX mail exchange
• dns
wireshark detail