Recent Posts?

This room will discuss the various resources MITRE has made available for the cybersecurity community.
MITREWhat is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
MITRE What is MITER ATT&CK Framework?
Miter; It is a non-profit organization created for engineering and technical guidance purposes. It was named ATT%CK, an abbreviation for enemy tactics, techniques and common knowledge, which began to be developed in 2013. In 2015, this project was offered to everyone free of charge and announced to the public free of charge.
The reason for such an action arises from the need to systematically categorize the behavior of the aggressors. It is a great resource that examines the methods used by the attackers, shows how an attack occurs, what vulnerabilities it uses, which techniques it uses. Using this resource, we can see which paths the attackers have used before and can predict their next move.
In short, MITER ATT&CK Framework; It is the place where all the cyber events that have happened so far are kept. It is known as the cyber attack encyclopedia.
What are MITER ATT&CK Matrices?
It contains techniques used by MITER ATT&CK Matrix attackers. These used techniques are categorized one by one. It is divided into 3 parts:
Enterprise ATT&CK
Enterprise ATT&CK matrisi Windows, Linux veya MacOS sistemlerinde çalıştırılan teknik ve taktiklerden oluşur. Enterprise ATT&CK matrisini incelediğimizde 14 tane farklı teknik gözümüze çarpmaktadır:
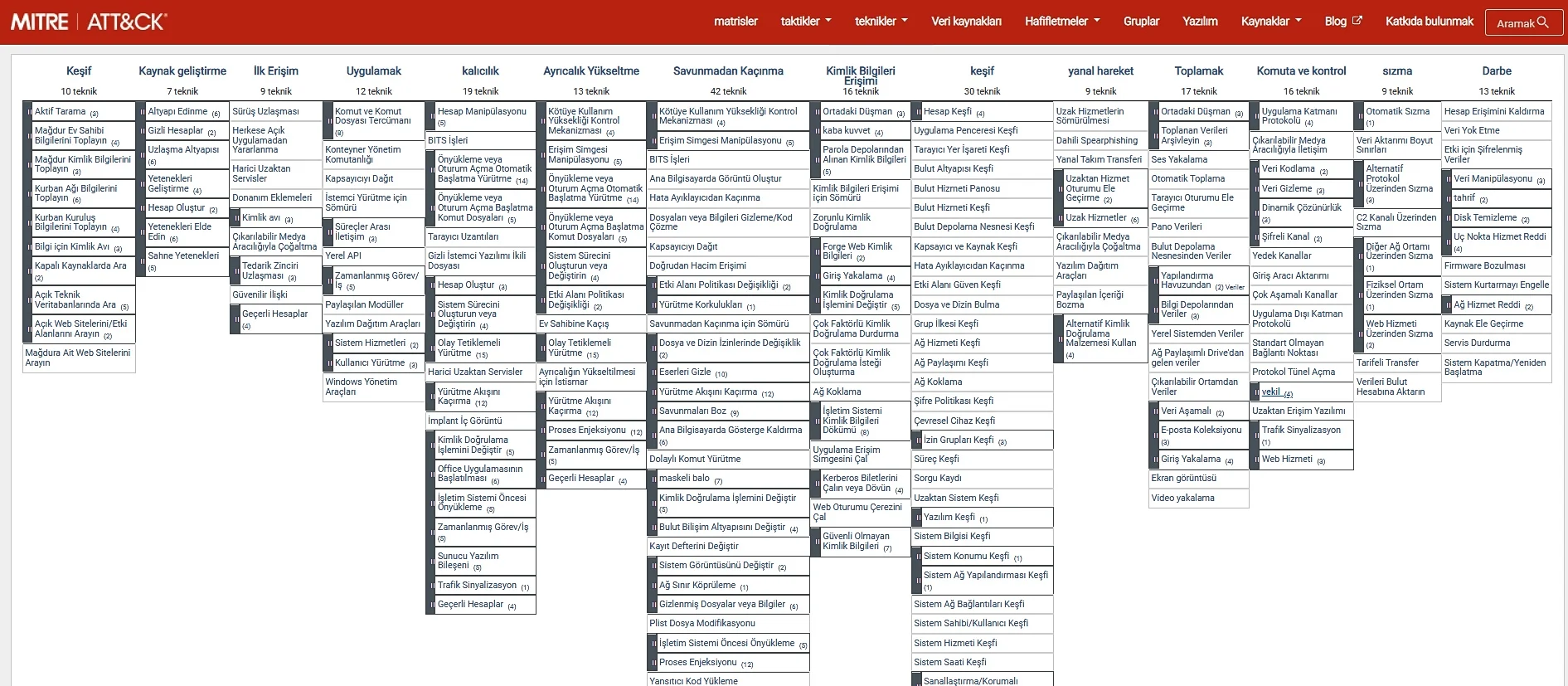
1-)Reconnaissance: Active and passive information gathering about the system
2-) Resource Development: It includes the techniques created so that attackers can use their targets in a supportive place.
3-) Initial Access: It consists of the techniques used to obtain their first place in the network.
4-)Execution: It includes techniques that cause it to be run through a local or remote system.
5-) Persistence: It consists of techniques to still exist in the system despite changes such as restarting, changing identity information.
6-) Privilege Escalation (Privilege Escalation): It consists of techniques to increase the authority in the system it provides access to.
7-)Defense Evasion: It shows the methods used to avoid being detected in the system it is in.
8-)Credential Access: It consists of techniques to steal credentials such as account names and passwords.
9-)Discovery It is the technical phase where the attacker collects information about the attacking system and internal network.
10-) Lateral Movement: It includes the techniques of attackers to enter and control remote systems in a network.
11-)Collection: These are the techniques that attackers can use and the techniques created to follow the attacker's purpose.
12-)Command and Control: It includes the techniques used by the attacker to communicate with other systems over the system he has seized.
13-)Exfiltration: It includes the techniques that attackers create to steal data from your network.
14-)Impact: It is the part where the attackers sabotage business and operational processes by using techniques of manipulating and put them into danger.
NOTE: The Pre-ATT&CK Matrix, which was previously considered separate, is now included in the Enterprise ATT&CK matrix.
Pre-ATT&CK: It includes the tactics and techniques that the attacker has prepared beforehand to prepare for an attack.
Mobile ATT&CK
It includes tactics and techniques applied by an attacker on mobile devices.
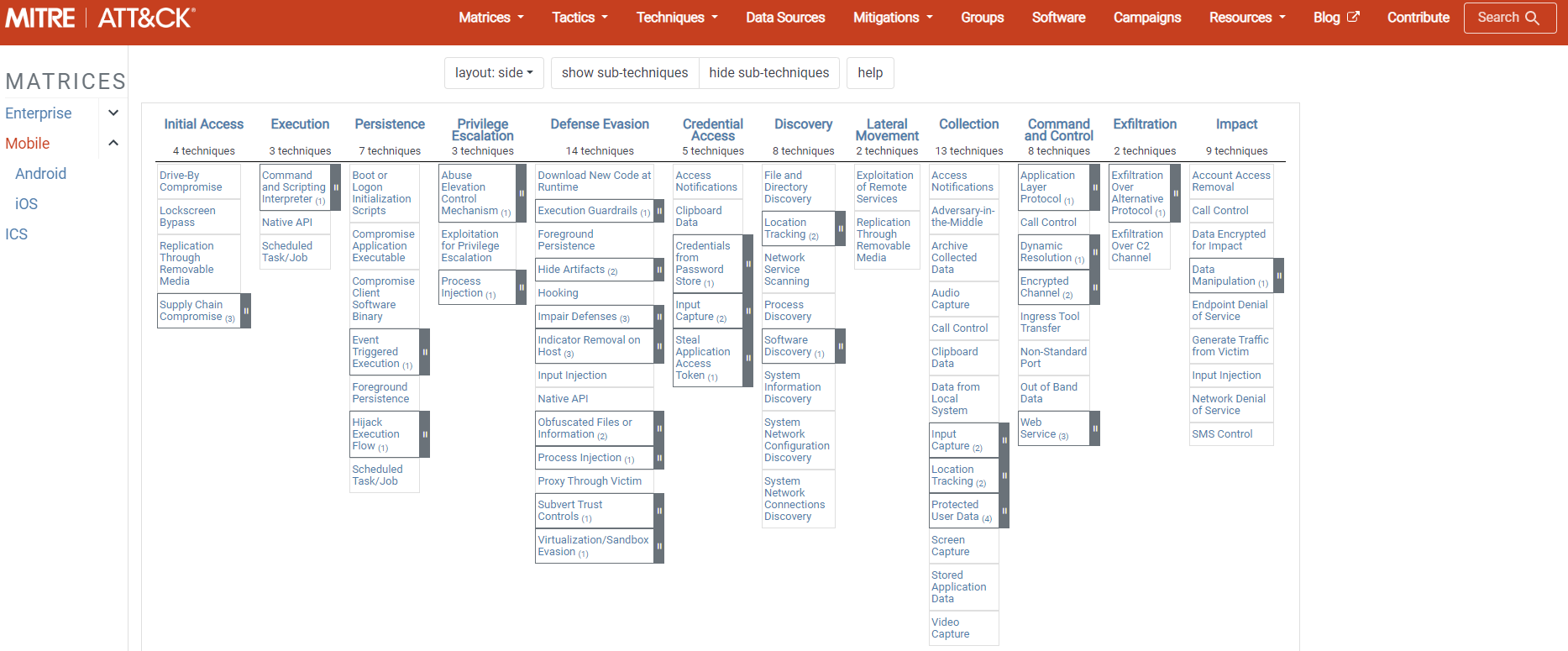
Unlike the Enterprise ATT&CK matrix, it uses 2 different techniques:
Network Effects: Includes techniques and tactics applied to intercept or modify network traffic to and from the mobile device.
Remote Services Effects: AIncludes techniques used to access services that are likely to be accessed remotely.
ICS ATT&CK
ICS is the abbreviation of industrial control systems (such as SCADA, DCS, PLC). The techniques and tactics of industrial attacks are contained in this matrix.
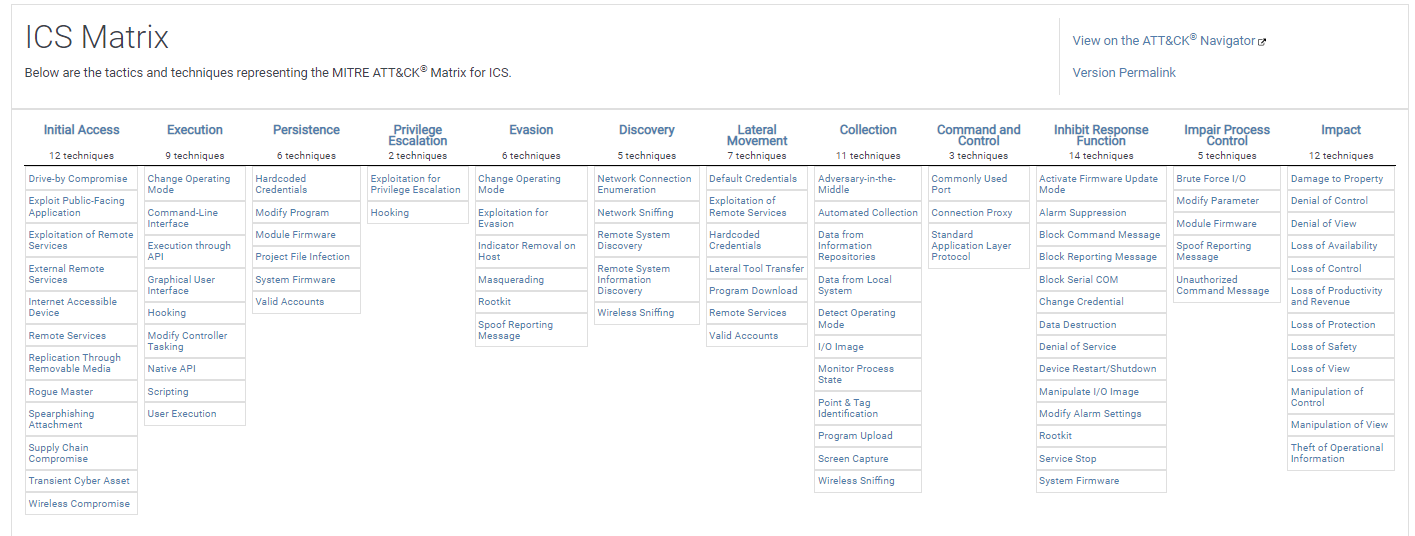
Unlike the Enterprise ATT&CK matrix, it uses 2 different techniques:
Inhibit Response Function: Techniques used by attackers to circumvent security measures applied on processes and products. These techniques aim to actively deter and prevent expected alarms and responses due to situations in the ICS environment.
Impair Process Control: Consists of techniques and tactics used by attackers to sabotage control logic and cause decisive effects on processes controlled in the target environment.
HOW TO USE MITER ATT&CK?
Now let's examine how we can use the MITER ATT&CK Framework platform.
Step 1: The first thing we will do is go to https://attack.mitre.org/ and select any matrix.
Step 2: Let's start by choosing one of these tactics and techniques. I choose the "Adversary-in-the-Middle" technique from the "Credential Access" tactic.
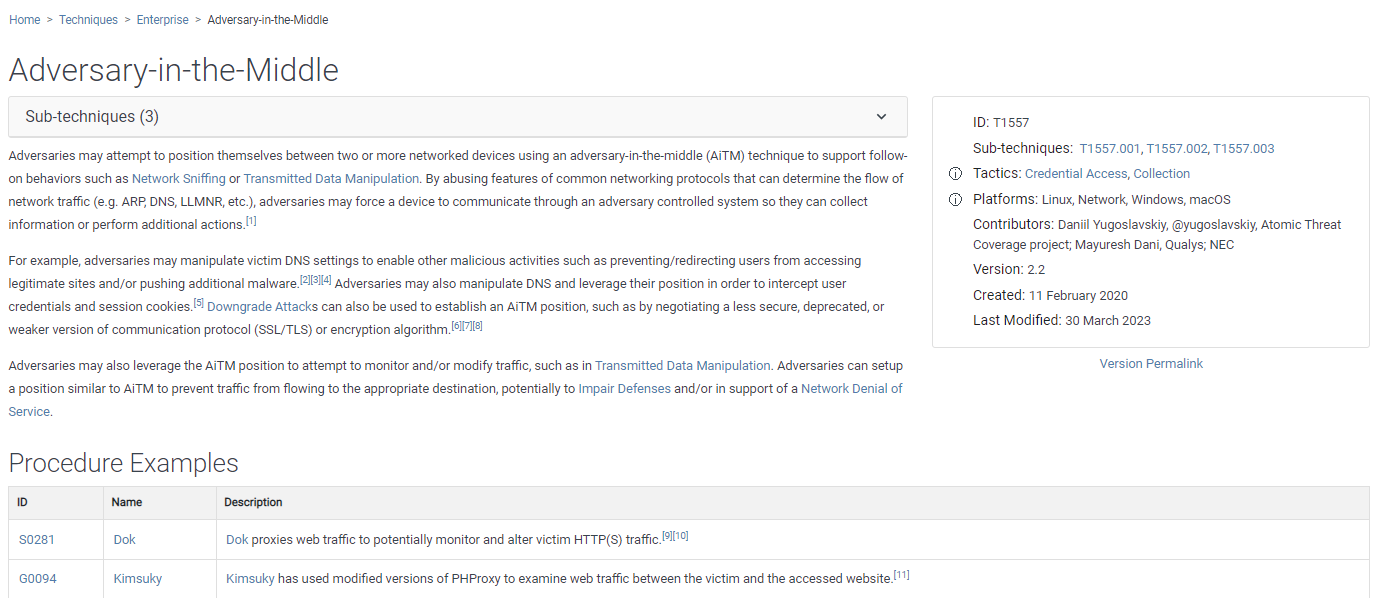
In addition, it shows the software and malicious procedures belonging to this attack on the Procedure Examples table of this attack.
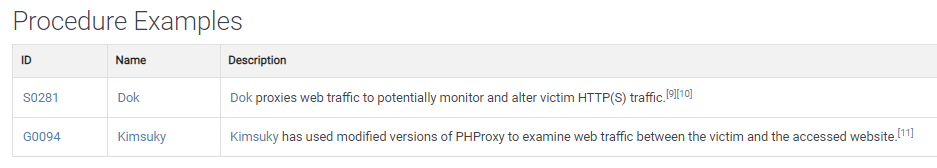
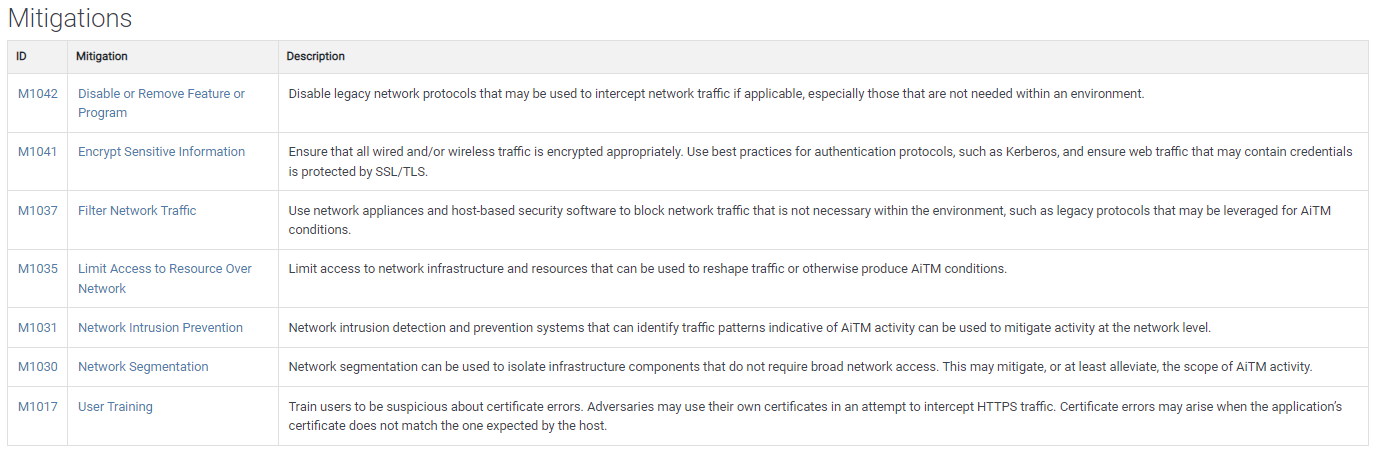
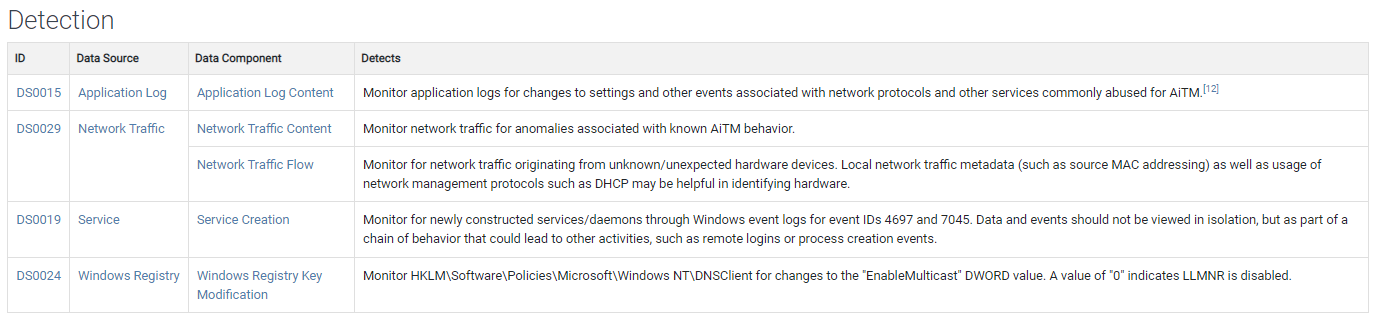
As we can see from the information above, there are all kinds of details about the attack.
What are MITER ATT&CK Techniques? Techniques
1) Reconnaissance (Discovery) It is the stage where the attacker tries to collect all the information that he can use in the actions he will take in the system. In this phase, it will collect active and passive information about the system in line with its objectives. Passive Information Collection; It is a method of collecting information about the target system from services on the internet or using websites to get information without providing direct access to the target system.
Active Information Gathering; It is the technique of collecting information by direct access or scanning to the target system. An attempt to collect information without permission because the system is interacted with is considered as a cybercrime pursuant to Article 243 of the Turkish Penal Code. Active information collected system information; It may contain sensitive data of the information system such as infrastructure and personnel information.
2) Resource Development Resource Development is the stage in which it consists of techniques that enable attackers to create resources that they can use to support their targets. These resources include supporting the infrastructure necessary to support the attacker's control of the system, server and network services, and account operations.
3) Initial Access It consists of techniques that use various input vectors to gain initial access in a network or system. At this stage, the attacker gains access by exploiting vulnerabilities of various systems such as spear phishing and public web servers.
4) Execution It consists of techniques that cause the attacker to execute code on a local or remote system. Techniques that run malicious code are often paired with techniques from all other tactics to achieve broader goals such as discovering a network or data leakage.
5) Persistence It is the phase in which various techniques are used by the attacker in order not to end his access to the system he has accessed and to continue his progress in the system. For example, with a malicious software it infects the system, it can enable the attacker to gain authority in the system at every start of the machine, change the identity information and take actions to prevent the existing access.
6) Privilege Escalation It includes techniques aimed at increasing the current authority of the attacker in the system accessed. It will need some authorization and permissions for the actions it aims to take in the system it is in. At this point; will exploit system weaknesses, misconfigurations, and vulnerabilities.
7) Defense Evasion It includes techniques that enable the attacker to circumvent the security measures taken for the system. Among the techniques used to evade defense in this phase are; uninstall/disable security software or hide/encrypt data and scripts. SYSTEM/root privilege local admin authority User account that appears to have administrative access User accounts that have access or function to a particular system are some examples of elevated privileges.
8) Credential Access It is the stage in which techniques to steal confidential access information such as the attacker's account username and password information are used. While trying to obtain attacker information, it aims to obtain credential dump with keylogging, Brute Force attack, attacks to password manager areas. At the same time, it is possible to use MFA deactivation, stealing website cookie information and network sniffing methods in line with its target.
9) Discovery It is the stage that consists of the techniques that the attacker will use to obtain information about the system and network he is targeting. It is the phase in which the attacker examines and discovers the existing accounts, security software and system information in the system.
10) Lateral Movement It includes techniques that allow the attacker to progress through the network in line with their goals. To perform the Lateral Movement, it is possible for the attacker to set up their own remote access tools, using legitimate credentials with local network and operating system tools that may be more confidential. SSH and RDP protocols hijacking, Windows remote management, remote service session hijacking are possible.
11) Collection It is the stage in which the attacker obtains the critical information determined in the target system and collects this information. Among its obtained sources are various types of drivers, browsers, audio, video and email information. Common collection methods include taking screenshots and keyboard inputs. This information; With various software such as Winzip, 7Zip and WinRAR, it compresses the files it obtains and facilitates the portability of the file. It is also possible for the attacker to obtain information from local systems and sharing points such as Sharepoint.
12) Command and Control It is the stage where the attacker consists of the techniques that he will use to communicate with other systems in the network he has captured. offensive, find
13) Exfiltration It consists of techniques that an attacker will use to steal data obtained from systems. To this end, the attacker packs, compresses or encrypts data to avoid detection.
14) Impact It is the stage that consists of techniques used by attackers to disrupt usability or compromise integrity by manipulating operational processes. by the attackers; It is used to achieve goals such as destroying, corrupting, and preventing access to data.
attack.mitre.org medium.com blockcyforen.com netsmart.com.tr siberkavram.com cyberartspro.com/ MENLO Security
Cyber security continues to be an area of increasing importance in both our individual and social lives today. ..
In this context, one of the conditions of being an educated individual is to be able to protect the security of information in the cyber environment and to be knowledgeable about manipulations.
For this reason, every individual active in social media should have basic cyber security information.
Read more
ManageEngine EventLog Analyzer
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more