Recent Posts?
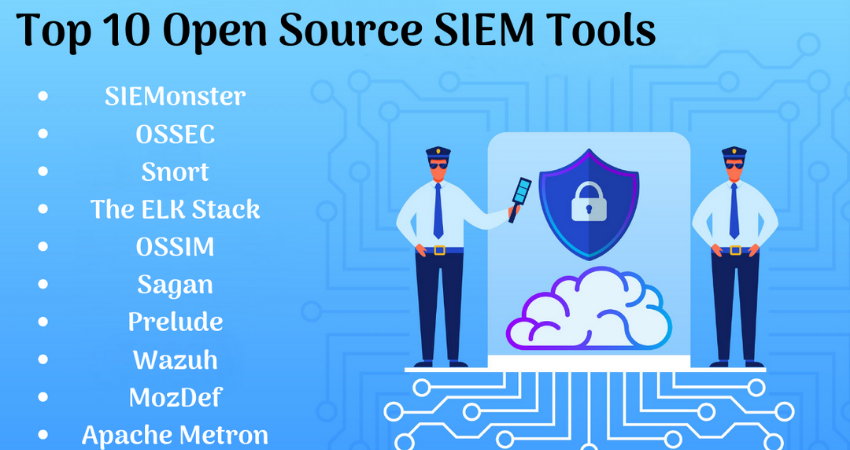
SIEM TOOLS
Graylog
Wazuh
Splunk
Datadog Log Collection & Management
SolarWinds Security Event Manager
SolarWinds Papertrail
ManageEngine Log360
Exabeam Fusion
Elastic Security
Fortinet FortiSIEM
Rapid7 InsightIDR
Trellix Helix
AT&T Cybersecurity AlienVault Unified Security Management
IBM Security QRadar SIEM
Logpoint
LogRhythm NextGen SIEM Platform
Loggly
ManageEngine EventLog Analyzer
FirstWave opEvents
Paessler PRTG Network Monitor
Fluentd
Logstash
Kibana
XpoLog
Managelogs
Fortinet FortiSIEM
Management Solution
The Hive
Jira
What is a SIEM solution? How SIEM works and Architecture? Relative Security
Security Information and Event Management or SIEM tools are essential for identifying cyber attacks.
What is Security Information and Event Management (SIEM)?
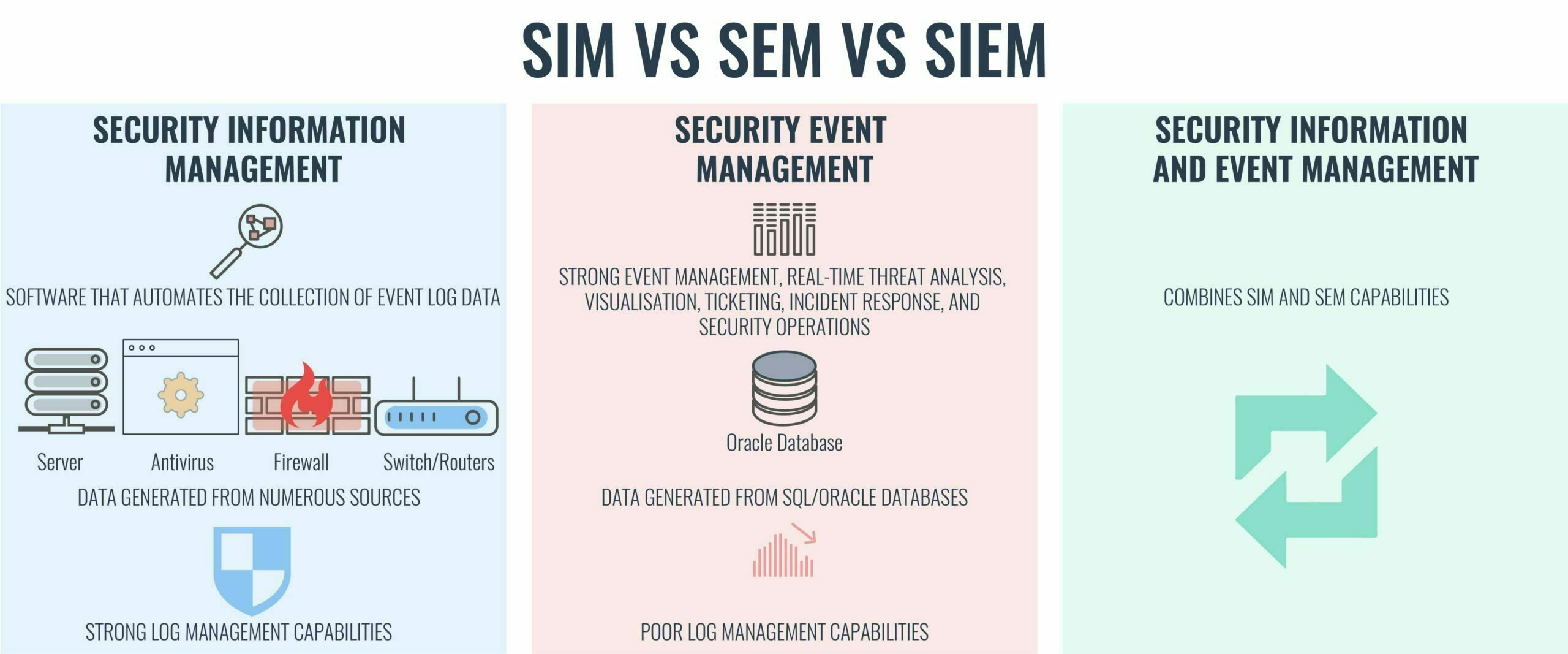
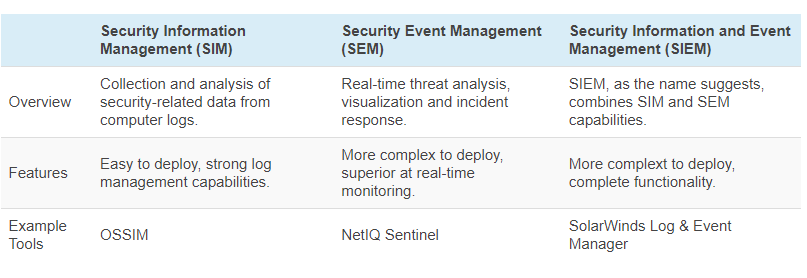
What is Security Information Management (SIM)?
Security Information Management (SIM) is the collection, monitoring, and analysis of security-related data from computer logs.
What is Security Event Management (SEM)?
Security Event Management (SEM) is the practice of network event management including real-time threat analysis, visualization, and incident response.
SIEM vs SIM vs SEM – what’s the difference?
SIEM, SIM, and SEM are often used interchangeably but there are some key differences.
SIEM capabilities
SIEM’s basic capabilities are as follows:
Log Collection
Normalization – Collecting logs and normalizing them into a standard format
Notifications and Alerts Notifying the user when security threats are identified
Security Incident Detection
Threat response workflow Workflow for handling past security events
SIEM records data from across a users’ internal network of tools and identifies potential issues and attacks. The system operates under a statistical model to analyze log entries. SIEM distributes collection agents and recalls data from the network, devices, servers, and firewalls.
All this information is then passed to a management console where it can be analyzed to address emerging threats. It’s not uncommon for advanced SIEM systems to use automated responses, entity behavior analytics and security orchestration. This ensures that vulnerabilities between cybersecurity tools can be monitored and addressed by SIEM technology.
Once the necessary information reaches the management console, it is then viewed by a data analyst who can provide feedback on the overall process. This is important because feedback helps to educate the SIEM system in terms of machine learning and increasing its familiarity with the surrounding environment.
Once the SIEM software system identifies a threat, it then communicates with other security systems on the device to stop the unwanted activity. The collaborative nature of SIEM systems makes them a popular enterprise-scale solution. However, the rise of pervasive cyber threats has made many small- and mid-sized businesses consider the merits of a SIEM system as well.
This change has been relatively recent because of the substantial costs of SIEM adoption. Not only must you pay a sizeable amount for the system itself; you need to allocate one or two members of staff to oversee it. As a result, smaller organizations have been less enthusiastic about SIEM adoption. But that has begun to change as SMEs can outsource to managed service providers.
Why is SIEM Important?
SIEM has become a core security component of modern organizations. The main reason is that every user or tracker leaves behind a virtual trail in a network’s log data. SIEM systems are designed to use this log data in order to generate insight into past attacks and events. A SIEM system not only identifies that an attack has happened, but allows you to see how and why it happened as well.
As organizations update and upscale to increasingly complex IT infrastructures, SIEM has become even more critical in recent years. Contrary to popular belief, firewalls and antivirus packages are not enough to protect a network in its entirety. Zero-day attacks can still penetrate a system’s defenses even with these security measures in place.
SIEM addresses this problem by detecting attack activity and assessing it against past behavior on the network. A SIEM system has the ability to distinguish between legitimate use and a malicious attack. This helps to increase a system’s incident protection and avoid damage to systems and virtual property.
The use of SIEM also helps companies to comply with a variety of industry cyber management regulations. Log management is the industry-standard method of auditing activity on an IT network. SIEM systems provide the best way to meet this regulatory requirement and provide transparency over logs in order to generate clear insights and improvements.
The essential features of SIEM Tools
Not all SIEM systems are built the same. As a result, there is no one-size-fits-all. A SIEM solution that’s right for one company may be incomplete to another. In this section, we break down the core features needed for a SIEM system.
Log Data Management As mentioned above, log data management is a core component of any enterprise-scale SIEM system. A SIEM system needs to pool log info from a variety of different data sources, each with their own way of categorizing and recording data. When looking for a SIEM system, you want one that has the ability to normalize data effectively (you might need a third-party program if your SIEM system isn’t managing disparate log data well).
Once the data is normalized, it is then quantified and compared against previously recorded data. The SIEM system can then recognize patterns of malicious behavior and raise notifications to alert the user to take action. This data can then be searched by an analyst who can define new criteria for future alerts. This helps to develop the system’s defenses against new threats.
Compliance Reporting
In terms of convenience and regulatory requirements, having a SIEM with extensive compliance reporting features is very important. In general, most SIEM systems have some kind of onboard report generating system that will help you to conform to your compliance requirements.
The source of requirements of the standards that you need to conform to will be a major influence on which SIEM system you install. If your security standards are dictated by customer contracts, you don’t have much leeway on which SIEM system you choose — if it doesn’t support the required standard, then it won’t be any you’re used to.
You may be required to demonstrate compliance to PCI DSS, FISMA, FERPA, HIPAA, SOX, ISO, NCUA, GLBA, NERC CIP, GPG13, DISA STIG or one of many other industry standards.
Threat Intelligence
If a breach or attack occurs, you can generate a report that details how it happened extensively. You can then use this data to refine internal processes and make adjustments to your network infrastructure to make sure it doesn’t happen again. This uses SIEM technology keeps your network infrastructure evolving to address new threats.
Fine Tuning Alert Conditions Having the ability to set the criteria for future security alerts is essential for maintaining an effective SIEM system through threat intelligence. Refining alerts is the main way you keep your SIEM system updated against new threats. Innovative cyber-attacks are emerging every day, so using a system that’s designed to add new security alerts stops you from getting left behind.
You also want to make sure that you find a SIEM software platform that can limit the number of security alerts you receive. If you’re inundated with alerts your team is going to be unable to address security concerns in a timely manner. Without fining tuning alerts you’re going to be subjected to sifting through masses of events from firewalls to intrusion logs.
Dashboard An extensive SIEM system is no good if you have a poor dashboard behind it. Having a dashboard with a simple user interface makes it much easier to identify threats. In practice, you’re looking for a dashboard with visualization. Straight away this allows your analyst to spot if any anomalies are occurring on the display. Ideally, you want a SIEM system that can be configured to show specific event data.
The best SIEM tools
Before choosing a SIEM tool, it’s important to evaluate your goals. For example, if you’re looking for a SIEM tool to meet regulatory requirements, generating reports will be one of your foremost priorities.
On the other hand, if you want to use a SIEM system to stay protected against emerging attacks, you need one with high functioning normalization and extensive user-defined notification facilities. Below we take a look at some of the best SIEM tools on the market.
Our methodology for selecting a SIEM toolWe reviewed the SIEM market and analyzed tools based on the following criteria:
A system that gathers both log messages and live traffic data
A log file management module
Data analysis utilities
The ability to report to data protection standards
Easy to install with an easy-to-use interface
A trial period for assessment
The right balance between functionality and value for money
For this reason, here is the best SIEM tools:

This room will discuss the various resources MITRE has made available for the cybersecurity community.
Download GRAYLOG
This log management package is available in four versions and two of them are free to use. Offered as a SaaS platform or as a virtual appliance
 Read more
Read more
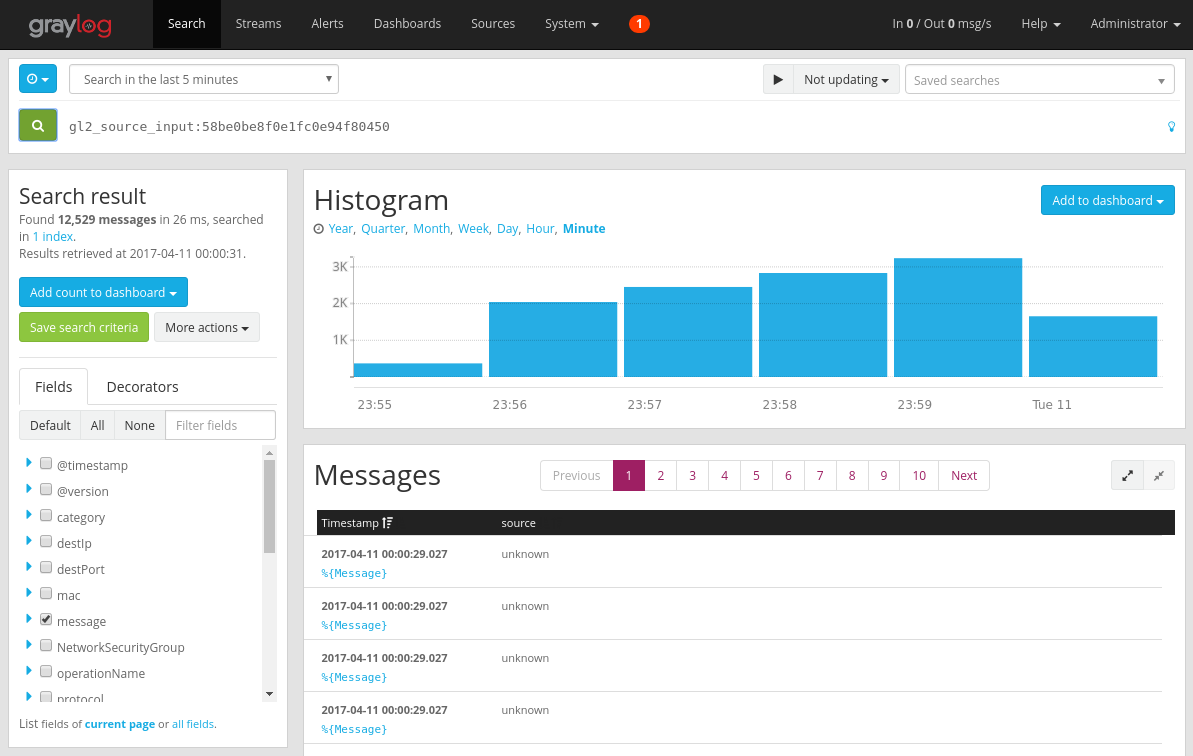
Search in graylog messages
After giving your Graylog server some time to collect the messages, you will be able to search the messages. To control messages sent to your Graylog server, on the Inputs configuration page, click the "Show received messages" button of the GELF UDP entry you created. You will be taken to a screen similar to the image below:
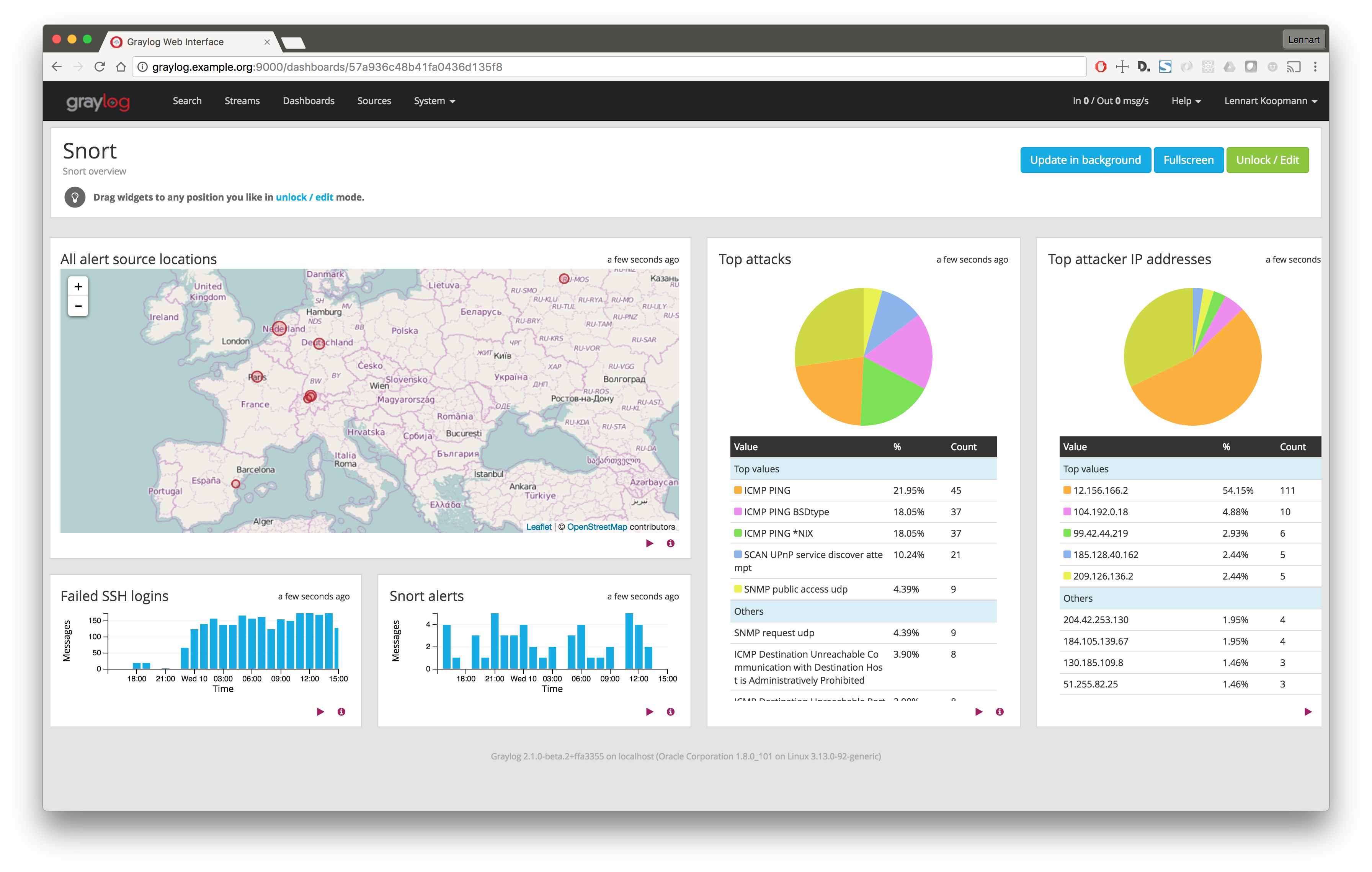
Clicking the blue "%{Message}" link expands each message to show the parameters of each flow tuple as shown in the image below:
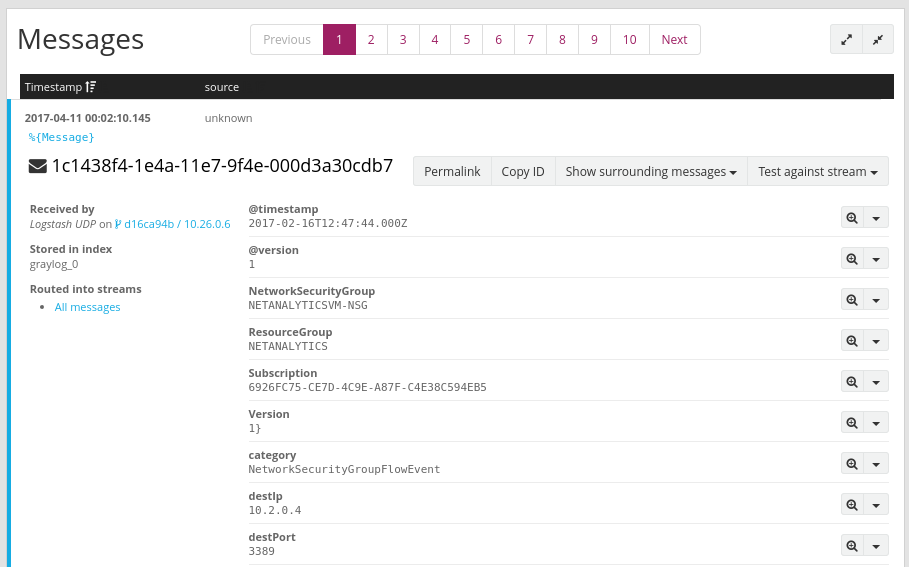

Wazuh
Wazuh Website
Wazuh Install
Wazuh is a free and open source platform used for threat prevention, detection, and response. It is capable of protecting workloads across on-premises, virtualized, containerized, and cloud-based environments.
Wazuh solution consists of an endpoint security agent, deployed to the monitored systems, and a management server, which collects and analyzes data gathered by the agents. Besides, Wazuh has been fully integrated with the Elastic Stack, providing a search engine and data visualization tool that allows users to navigate through their security alerts.
Elastic Stack is a software package for collecting, parsing, indexing, storing, searching and presenting log data. Elastic Stack is a combination of three popular open source projects for daily management known as Elasticsearch, Logstash and Kibana. Together they form a real-time and user interface for Wazuh alarms. It comes with ready-to-use dashboards for Wazuh integration with Elastic Stack, PCI DSS compliance and CIS criteria.
Read more https://github.com/wazuh/wazuh Read more bgasecurity.comIntroduction To Wazuh SIEM HackerSploit
Installing & Configuring Wazuh HackerSploit
Wazuh capabilitiesA brief presentation of some of the more common use cases of the Wazuh solution.
Intrusion detection Wazuh agents scan the monitored systems looking for malware, rootkits and suspicious anomalies. They can detect hidden files, cloaked processes or unregistered network listeners, as well as inconsistencies in system call responses. In addition to agent capabilities, the server component uses a signature-based approach to intrusion detection, using its regular expression engine to analyze collected log data and look for indicators of compromise.
Log data analysis Wazuh agents read operating system and application logs, and securely forward them to a central manager for rule-based analysis and storage. When no agent is deployed, the server can also receive data via syslog from network devices or applications.
The Wazuh rules help make you aware of application or system errors, misconfigurations, attempted and/or successful malicious activities, policy violations and a variety of other security and operational issues.
File integrity monitoringWazuh monitors the file system, identifying changes in content, permissions, ownership, and attributes of files that you need to keep an eye on. In addition, it natively identifies users and applications used to create or modify files.
File integrity monitoring capabilities can be used in combination with threat intelligence to identify threats or compromised hosts. In addition, several regulatory compliance standards, such as PCI DSS, require it.
Vulnerability detection Wazuh agents pull software inventory data and send this information to the server, where it is correlated with continuously updated CVE (Common Vulnerabilities and Exposure) databases, in order to identify well-known vulnerable software.
Automated vulnerability assessment helps you find the weak spots in your critical assets and take corrective action before attackers exploit them to sabotage your business or steal confidential data.
Configuration assessment
Wazuh monitors system and application configuration settings to ensure they are compliant with your security policies, standards and/or hardening guides. Agents perform periodic scans to detect applications that are known to be vulnerable, unpatched, or insecurely configured.
Additionally, configuration checks can be customized, tailoring them to properly align with your organization. Alerts include recommendations for better configuration, references and mapping with regulatory compliance.
Incident response Wazuh provides out-of-the-box active responses to perform various countermeasures to address active threats, such as blocking access to a system from the threat source when certain criteria are met.
In addition, Wazuh can be used to remotely run commands or system queries, identifying indicators of compromise (IOCs) and helping perform other live forensics or incident response tasks.
Regulatory compliance Wazuh provides some of the necessary security controls to become compliant with industry standards and regulations. These features, combined with its scalability and multi-platform support help organizations meet technical compliance requirements.
Wazuh is widely used by payment processing companies and financial institutions to meet PCI DSS (Payment Card Industry Data Security Standard) requirements. Its web user interface provides reports and dashboards that can help with this and other regulations (e.g. GPG13 or GDPR).
Cloud security Wazuh helps monitoring cloud infrastructure at an API level, using integration modules that are able to pull security data from well known cloud providers, such as Amazon AWS, Azure or Google Cloud. In addition, Wazuh provides rules to assess the configuration of your cloud environment, easily spotting weaknesses.
In addition, Wazuh light-weight and multi-platform agents are commonly used to monitor cloud environments at the instance level.
Containers security Wazuh provides security visibility into your Docker hosts and containers, monitoring their behavior and detecting threats, vulnerabilities and anomalies. The Wazuh agent has native integration with the Docker engine allowing users to monitor images, volumes, network settings, and running containers.
Wazuh continuously collects and analyzes detailed runtime information. For example, alerting for containers running in privileged mode, vulnerable applications, a shell running in a container, changes to persistent volumes or images, and other possible threats.
Intrusion Detection with Wazuh | Blue Team Series with Hackersploit Linode
Read more Turkish | BGA Security
What is Splunk? What are the advantages? What are Splunk Solutions?
Splunk is a software platform that provides solutions in cyber security and IT operations. The company's purpose includes incorporating data for all existing questions, decisions and actions.
Splunk is a software platform that provides solutions in cyber security and IT operations. The company's purpose includes incorporating data for all existing questions, decisions and actions. It mainly offers security, IT operations and Devops solutions. This solution allows organizations to leverage machine data by detecting data patterns, providing metrics, and diagnosing problems.
Machine data consists of complex, difficult to understand, unstructured data. It is not possible for businesses to use this data without processing. The data is processed by the software solution and brought into a form that businesses can benefit from.
Splunk for Security: What is Enterprise Security? | Ft. Advanced Detection & Improved Investigations Somerford Associates
Somerford Associates
What are the Splunk Advantages?
Thanks to its advantages, Splunk is used by businesses of different sizes. The data produced by sensors, websites, applications and devices are processed and used in data-based decision-making processes.
• Allows businesses to make data-based decisions by collecting data from different devices and platforms.
• Data can be drawn from more than one system simultaneously.
• Allows big data training.
• Data can be provided as input in different formats such as json, .csv.
• Required resource estimates can be made to scale up the infrastructure.
• System performance is analyzed and points that cause performance loss are detected.
• Business metrics are tracked.
• Panel can be created to visualize data and generate related reports.
• Data can be retrieved and stored for later use.
What are Splunk Solutions? Splunk solutions can be examined in three different categories:
1. Cyber Security Solutions Splunk cybersecurity solutions allow businesses to innovate by minimizing risk. Data is integrated into security solutions, providing analytics and operational solutions. Understanding risks, resisting infiltrations and complying with guidelines are among the most preferred cyber security solutions.
2. IT Operations It contributes to the development and transformation processes of enterprises by making data-based decisions in IT operations. Necessary software solutions are offered for technical agility, capacity and speed. Business monitoring and AIOPs are among the solutions used in IT operations.
3. Devops Devops, on the other hand, allows processes to be accelerated to deliver unmatched user experience. Complex and cloud systems are better managed. User experience is maximized through in-depth insights. Infrastructure monitoring, incident response and application modernization are among the Spunk devops solutions.
What are the Splunk Advantages?
Edureka
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
SolarWinds Security Event Manager
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
LogRhythm NextGen SIEM Platform
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
AT&T Cybersecurity AlienVault Unified Security Management
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more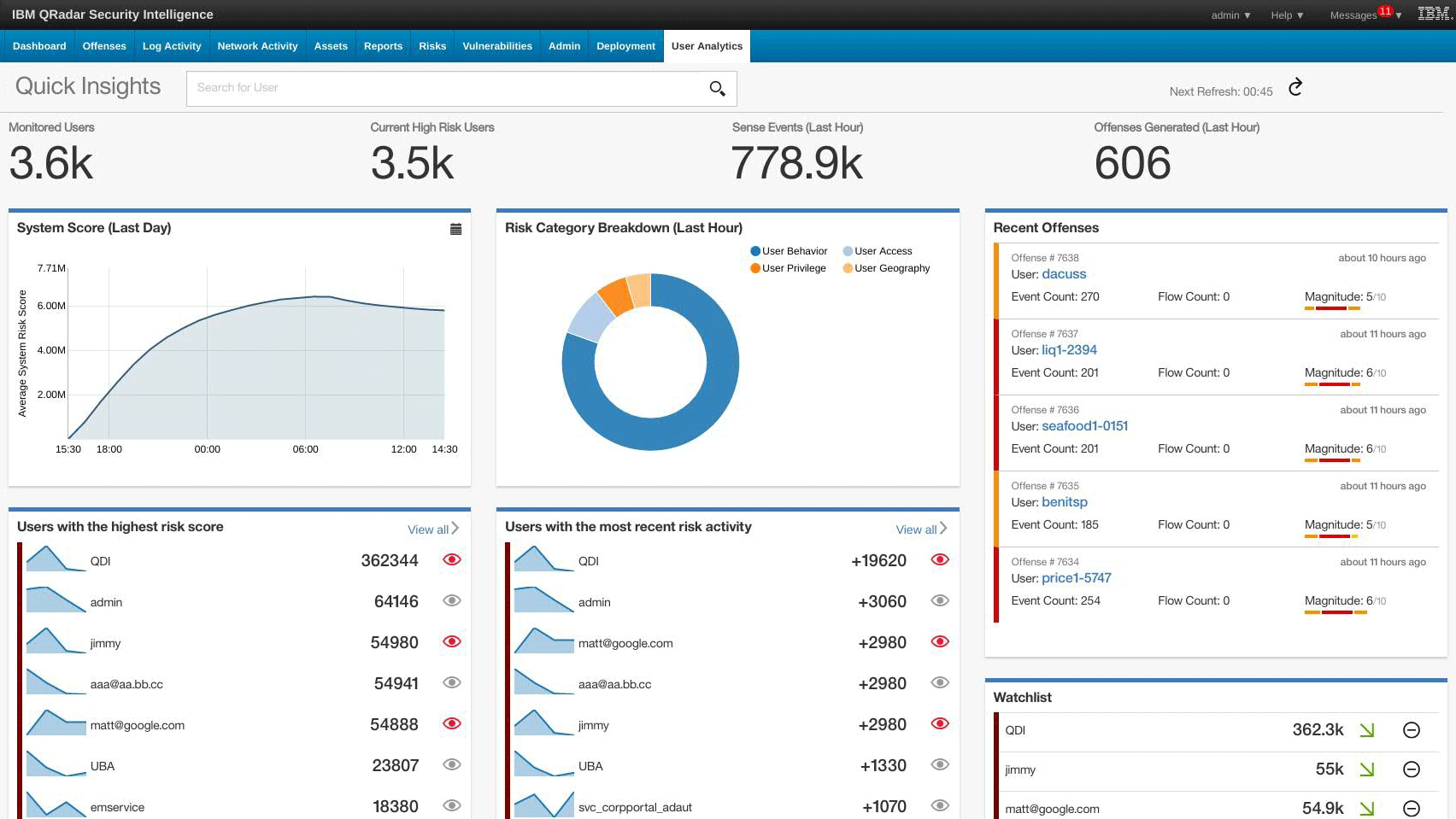
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
ManageEngine EventLog Analyzer
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more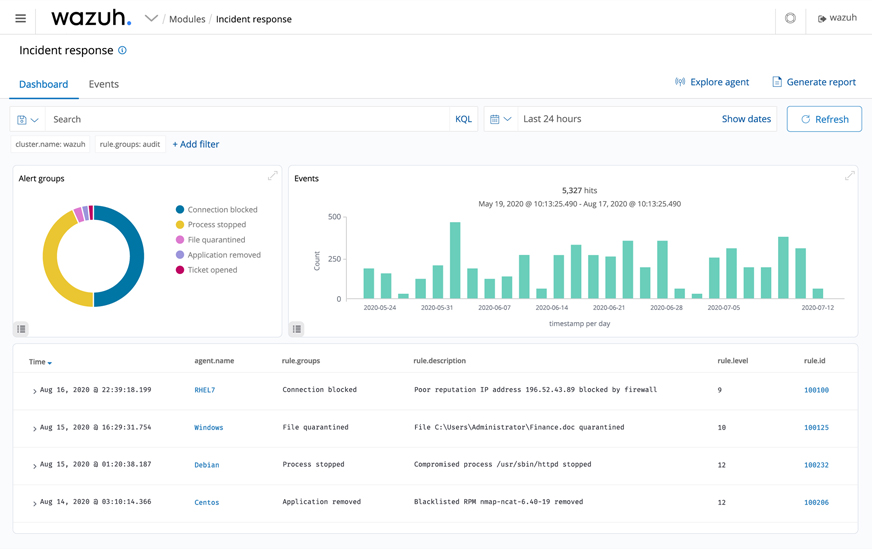
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more
The Hive is an open source, scalable and free incident response platform designed for cyber incident response teams to get their work done quickly. Using teamwork when investigating a cyber case greatly improves the quality of incident response work. TheHive's designers are an in-depth analytics and SOC orchestration platform focused on teams working together and collaborating to conduct timely investigations. Each investigation process corresponds to a case that can be divided into one or more tasks. These tasks are assigned to security operations analysts and then asked to investigate them simultaneously.
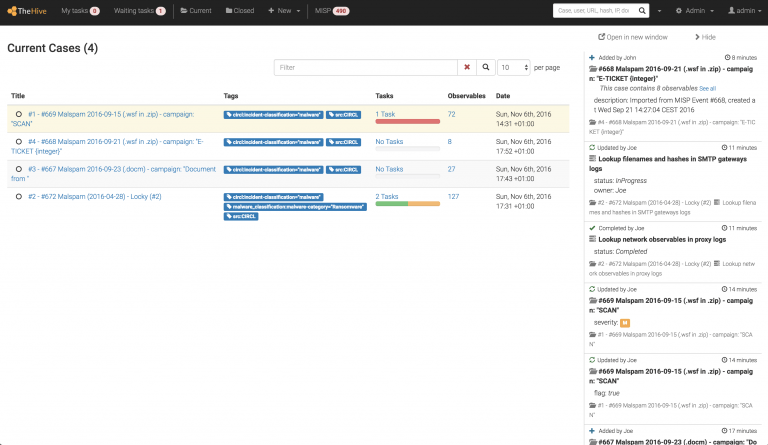
TheHive also has a Python API client that allows analysts to create cases and send alerts from different sources such as email or SIEM. Additional utility tools made by TheHive Project are developing Cortex, an automation tool for batch analysis, and Hippocampe, a threat intelligence feed aggregator.
The Hive – Collaborating:
How to use TheHive : Security Incident Response Platform
The Hive – Detailing
In TheHive project, each inquiry corresponds to an event. Cases can be generated from MISP (Malware Information Sharing Platform) events, SIEM alerts, email reports, and any other notable security event.
Each case can be allocated to one or more tasks. Rather than adding the same tasks when the case is created, analysts can use TheHive's template engine to create them once and for all. Case templates can be used to associate metrics with specific case types to increase team effectiveness, identify the type of investigations that take significant time, and automate tedious tasks. Each task can be assigned to a specific analyst.
Team members can also act on a task without waiting for others to be assigned to them. Tasks can contain multiple studies that analysts can contribute to defining an event, such as what the task is, adding results, evidence, or notable files. Apart from these, records can be written using a rich text editor or Markdown, which is very advantageous for editorial work.

This room will discuss the various resources MITRE has made available for the cybersecurity community.
What is MITER ATT&CK Framework?
What are MITER ATT&CK Matrices?
How to use MITER ATT&CK?
What are MITER ATT&CK Techniques?
For this reason, every individual active in social media should have basic cyber security information.
Read more